 Mobile devices are becoming more powerful with each day and rivaling any PC in its capabilities and services offered. It is not only your working platform anymore but also a powerful storage device which means that it can also be the potential target of viruses and malware.
Mobile devices are becoming more powerful with each day and rivaling any PC in its capabilities and services offered. It is not only your working platform anymore but also a powerful storage device which means that it can also be the potential target of viruses and malware.
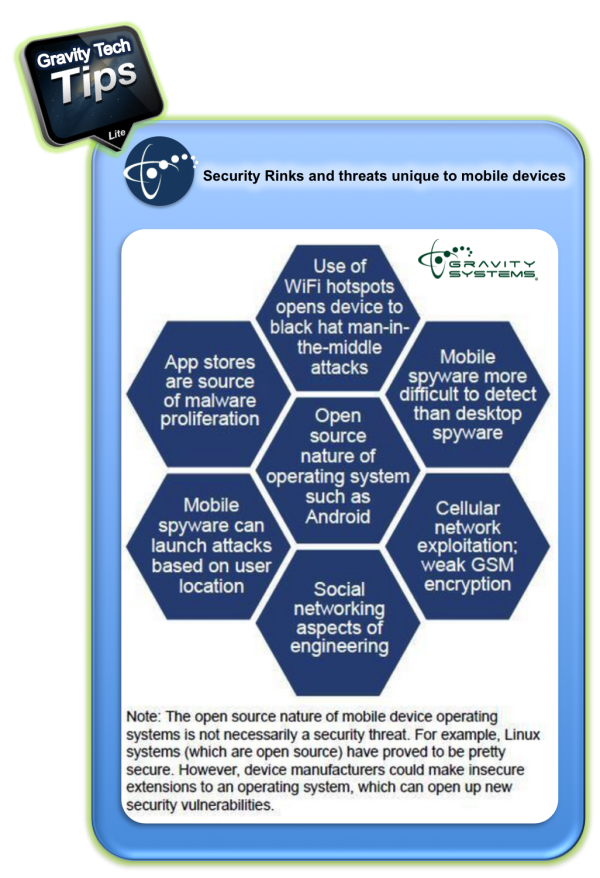
Mobile device security has become imperative because the nature of the security hazards are divergent. Let us see what some of the most common methods are by which your mobile device could be accessed via cyber attacks.
- Malware and viruses
These are the biggest threat to your mobile security, why? Because they are ever evolving and adapting by nature and you can never be sure about their identity. They can even disguise themselves as Android Apps.
- Accessing Wi-Fi
How sure are you that the open connection you accessed at the café was not used by cyber criminals to get access to your private information including sensitive data and even your credit card information?
- Information accessed from lost devices
This is the most common of all problems with mobile devices being commonly lost and misplaced. If it gets into the wrong hands there are always chances of information being accessed and misused.
- Unsecured file transfers
How secure is the file transfer that you are doing online? While syncing with cloud storage providers is the answer to the storage problem on the device, how sure can you be about the encrypted file transfer? In fact, this is one of the leading threats to mobile safety.
- Unclear company policy
Seems an unlikely reason for threat to mobile device security? Believe it or not it’s true, having a company policy in place to make employees responsible and accountable for their devices goes a long way in curbing this hazard.
Seems intimidating? Moreover where do you go to for a comprehensive IT support in Austin? Here’s where we step in; Gravity USA with an impressive track record of providing impeccable Tech Services in Texas, our belief is that solutions, even for big problems are actually quite simple ones. So to begin with, you need a locking mechanism in your mobile device. It could be as simple as a pin or a password, but it goes a long way in securing your device. Let us review a few more options that you could begin with.
- Setup a company policy
As they say the best place to begin is always at home, so to begin with the company needs to have a policy for mobile management and security strategy. It creates the groundwork for protecting the company’s critical data.
- A secure corporate connection is a must
The use of encryption such as SSL can never be over-emphasized. In fact it is the only way to keep the communication between the mobile device and the company network or cloud systems secure and inaccessible to outsiders.
- Protect against Malware
It is essential to have Malware protection if you are using web interfaces which are vulnerable to common web attack mechanisms like XSS or SQL which helps to step up the process of getting information from your devices.
- Ability to remotely wipe/disable
By installing a security software or by setting up a mobile device management platform by availing Information Technology services it is possible to wipe data from a mobile device.
These tips are a good way to begin the process of securing your mobile devices. However for a wall-to-wall security cover for an organization, there is a need for round the clock surveillance from a professional IT security appraisal and vigilance team.
Do give us a call to know more about the options for IT support in Austin that you and your organization can avail from Gravity Systems.



