
A common type of virus is a malware, which causes huge data loss and unrecoverable damage to your company’s system files. It is often believed that all these malwares are originated from inside. But fighting viruses from Internet is considered to be only a part of the battle against virus. Some of the viruses are originated from the inside as well, as the recent evidence suggests. Dealing with threats closer to home is also necessary.
Depiction of a network virus
The type of malware varies. Some of the common types are Trojan Horses and Worms. They enter your system network from many sources like USB memory sticks, CDs, memory cards, smart phones and many tablets and also from internet. Antivirus has the function of scanning any external devices before being allowed into the file systems. This is not enough as some viruses go undetected in these scans. This is because these days viruses are more advanced and are evolving to the countermeasures built by antivirus software. The viruses are evolved to disrupt and destroy data, circumvent confidential information.
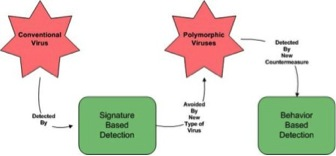
An illustration of evolution of viruses.
The basic method used by antivirus is by scanning and recognizing patterns in all files. Some files will have different patterns which will not be seen in other files. Based on this, the antivirus starts to heal the files by terminating the irregular pattern. Since the software functions to terminate the pattern, it leaves a fingerprint, a digital fingerprint. These are used by virus writers to develop or evolve malwares in order to disguise these patterns. The above image shows one such operation. Today’s viruses are complicated and each of them designed and built to perform a specific function. Some of them are discussed here.
- Keyloggers - transmission of keystrokes to the attacker
- Video frame grabbers- transmit a perfect screenshot of the display to the attacker
- Trojan horse – contains deadly malwares like spyware and keyloggers.
HOW TO DEAL WITH THESE VIRUSES BEFORE ENORMOUS DAMAGE IS DONE?
The common and basic solution would be integrating scanning checkpoints to the client devices at the entry of traffic. This way, the virus can be detected at an early stage and can be terminated instantly. Another way will be endpoint security. The simple definition to end point security is it’s a new approach towards network security which compiles certain basic standards before network access is granted. There are various companies and brands that offer endpoint security.
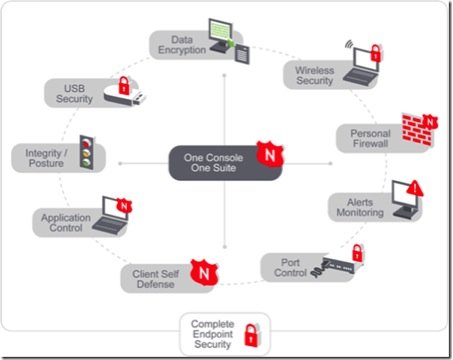
Branching structure of an endpoint security.
The above image clearly explains the role of an endpoint security and the various sources of various it prohibits. IT solutions are never ending and will be innovated every day and so will be the viruses. Therefore, a constant set of functions and processes is necessary to counteract these deadly viruses. It is better if these viruses are prevented altogether by having a strong and secure protection to our system files.
Gravity USA- IT support Austin is one of the most efficient and affordable IT solutions in all of Texas. The amicable atmosphere in their office and the friendly nature of all of their employees makes it a pleasure to be a client for them. Gravity USA – IT Support Austin is considered to be one of the best IT support and solutions Austin, Texas. Their services are meant to minimize virus risk and constant effort is done to counteract the new ones in future.



